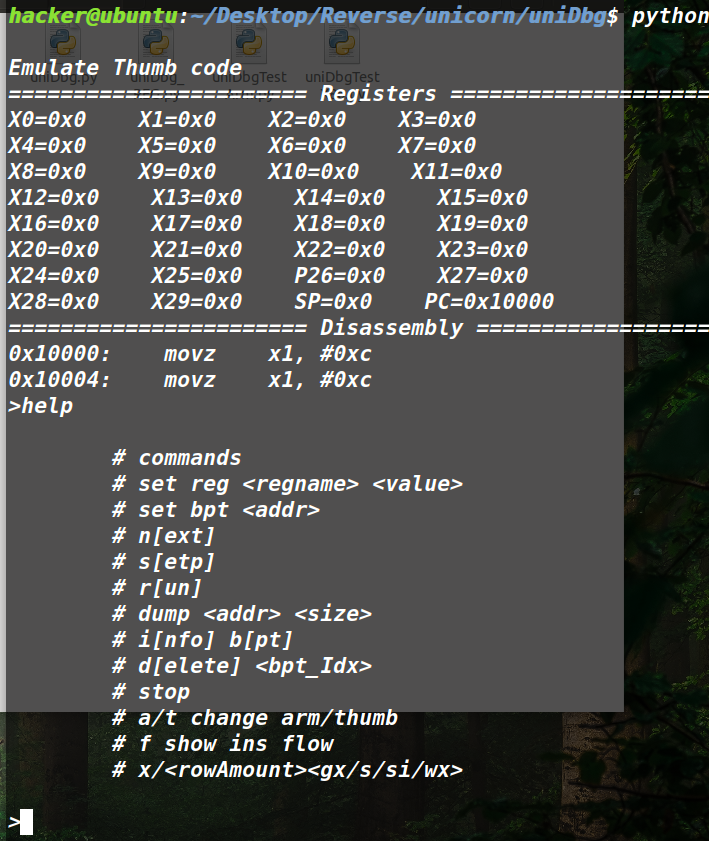
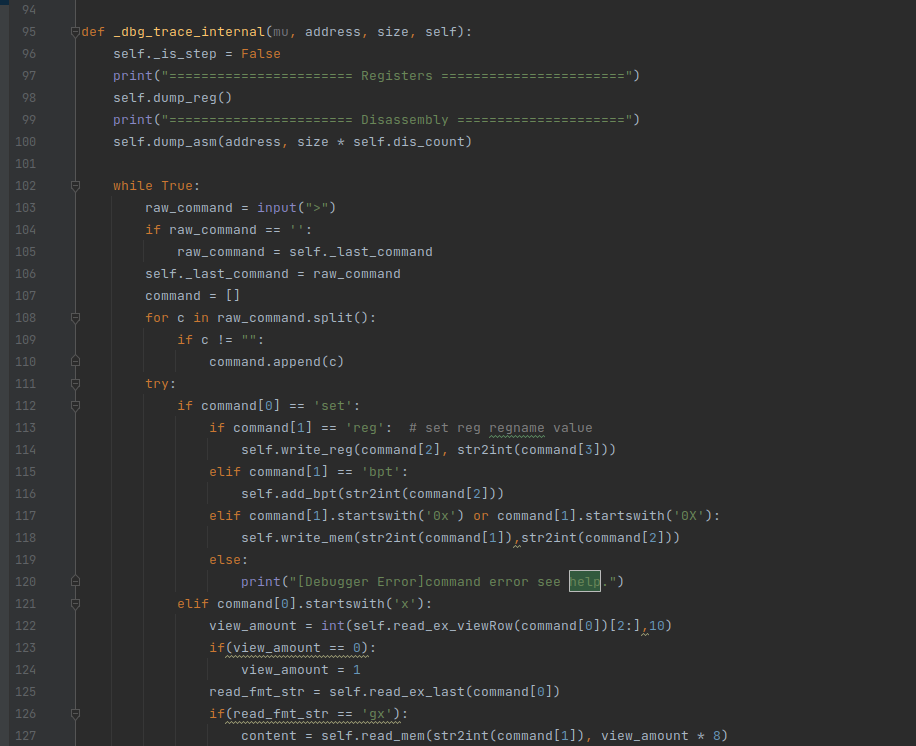
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
| from unicorn import *
REG_ARM = {arm_const.UC_ARM_REG_R0: "R0",
arm_const.UC_ARM_REG_R1: "R1",
arm_const.UC_ARM_REG_R2: "R2",
arm_const.UC_ARM_REG_R3: "R3",
arm_const.UC_ARM_REG_R4: "R4",
arm_const.UC_ARM_REG_R5: "R5",
arm_const.UC_ARM_REG_R6: "R6",
arm_const.UC_ARM_REG_R7: "R7",
arm_const.UC_ARM_REG_R8: "R8",
arm_const.UC_ARM_REG_R9: "R9",
arm_const.UC_ARM_REG_R10: "R10",
arm_const.UC_ARM_REG_R11: "R11",
arm_const.UC_ARM_REG_R12: "R12",
arm_const.UC_ARM_REG_R13: "R13",
arm_const.UC_ARM_REG_R14: "R14",
arm_const.UC_ARM_REG_R15: "R15",
arm_const.UC_ARM_REG_PC: "PC",
arm_const.UC_ARM_REG_SP: "SP",
arm_const.UC_ARM_REG_LR: "LR"
}
REG_ARM64 = {arm64_const.UC_ARM64_REG_X0: "X0",
arm64_const.UC_ARM64_REG_X1: "X1",
arm64_const.UC_ARM64_REG_X2: "X2",
arm64_const.UC_ARM64_REG_X3: "X3",
arm64_const.UC_ARM64_REG_X4: "X4",
arm64_const.UC_ARM64_REG_X5: "X5",
arm64_const.UC_ARM64_REG_X6: "X6",
arm64_const.UC_ARM64_REG_X7: "X7",
arm64_const.UC_ARM64_REG_X8: "X8",
arm64_const.UC_ARM64_REG_X9: "X9",
arm64_const.UC_ARM64_REG_X10: "X10",
arm64_const.UC_ARM64_REG_X11: "X11",
arm64_const.UC_ARM64_REG_X12: "X12",
arm64_const.UC_ARM64_REG_X13: "X13",
arm64_const.UC_ARM64_REG_X14: "X14",
arm64_const.UC_ARM64_REG_X15: "X15",
arm64_const.UC_ARM64_REG_X16: "X16",
arm64_const.UC_ARM64_REG_X17: "X17",
arm64_const.UC_ARM64_REG_X18: "X18",
arm64_const.UC_ARM64_REG_X19: "X19",
arm64_const.UC_ARM64_REG_X20: "X20",
arm64_const.UC_ARM64_REG_X21: "X21",
arm64_const.UC_ARM64_REG_X22: "X22",
arm64_const.UC_ARM64_REG_X23: "X23",
arm64_const.UC_ARM64_REG_X24: "X24",
arm64_const.UC_ARM64_REG_X25: "X25",
arm64_const.UC_ARM64_REG_X26: "P26",
arm64_const.UC_ARM64_REG_X27: "X27",
arm64_const.UC_ARM64_REG_X28: "X28",
arm64_const.UC_ARM64_REG_X29: "X29",
arm64_const.UC_ARM64_REG_SP: "SP",
arm64_const.UC_ARM64_REG_PC: "PC",
}
REG_AMD64 = {x86_const.UC_X86_REG_RAX: "RAX",
x86_const.UC_X86_REG_RBX: "RBX",
x86_const.UC_X86_REG_RCX: "RCX",
x86_const.UC_X86_REG_RDX: "RDX",
x86_const.UC_X86_REG_RDI: "RDI",
x86_const.UC_X86_REG_RSI: "RSI",
x86_const.UC_X86_REG_R8: "R8",
x86_const.UC_X86_REG_R9: "R9",
x86_const.UC_X86_REG_R10: "R10",
x86_const.UC_X86_REG_R11: "R11",
x86_const.UC_X86_REG_R12: "R12",
x86_const.UC_X86_REG_R13: "R13",
x86_const.UC_X86_REG_R14: "R14",
x86_const.UC_X86_REG_R15: "R15",
x86_const.UC_X86_REG_RBP: "RBP",
x86_const.UC_X86_REG_RSP: "RSP",
x86_const.UC_X86_REG_RIP: "RIP",
}
REG_MIPS = {
mips_const.UC_MIPS_REG_ZERO: "ZERO",
mips_const.UC_MIPS_REG_V0: "V0",
mips_const.UC_MIPS_REG_V1: "V1",
mips_const.UC_MIPS_REG_AT: "AT",
mips_const.UC_MIPS_REG_A0: "A0",
mips_const.UC_MIPS_REG_A1: "A1",
mips_const.UC_MIPS_REG_A2: "A2",
mips_const.UC_MIPS_REG_A3: "A3",
mips_const.UC_MIPS_REG_T0: "T0",
mips_const.UC_MIPS_REG_T1: "T1",
mips_const.UC_MIPS_REG_T2: "T2",
mips_const.UC_MIPS_REG_T3: "T3",
mips_const.UC_MIPS_REG_T4: "T4",
mips_const.UC_MIPS_REG_T5: "T5",
mips_const.UC_MIPS_REG_T6: "T6",
mips_const.UC_MIPS_REG_T7: "T7",
mips_const.UC_MIPS_REG_S0: "S0",
mips_const.UC_MIPS_REG_S1: "S1",
mips_const.UC_MIPS_REG_S2: "S2",
mips_const.UC_MIPS_REG_S3: "S3",
mips_const.UC_MIPS_REG_S4: "S4",
mips_const.UC_MIPS_REG_S5: "S5",
mips_const.UC_MIPS_REG_S6: "S6",
mips_const.UC_MIPS_REG_S7: "S7",
mips_const.UC_MIPS_REG_T8: "T8",
mips_const.UC_MIPS_REG_T9: "T9",
mips_const.UC_MIPS_REG_GP: "GP",
mips_const.UC_MIPS_REG_SP: "SP",
mips_const.UC_MIPS_REG_FP: "FP",
mips_const.UC_MIPS_REG_RA: "RA",
}
REG_TABLE = {UC_ARCH_ARM: REG_ARM, UC_ARCH_X86: REG_AMD64,UC_ARCH_MIPS: REG_MIPS,UC_ARCH_ARM64:REG_ARM64}
|